In our prior blog post, we talked about how mobile security is often underemphasized. One of the threats mentioned was malware. Many IT people have been led to believe that having a device in MDM and disabling non-market app installation takes care of this risk, but it turns out that’s not entirely true.
The NortonLifelock Research Group and the IMDEA Software Institute published a fascinating analysis of Android malware based on information gathered from millions of devices, and, incredibly, they found that the most common vector for Android malware is the official Google Play Store.
According to their findings, a full 87% of all installs, and 67% of unwanted installs of Android malware. The researchers were quick to point out that while the Play Store is the primary vector for malware, as a whole the Play Store is by far the safest distribution vector in their study. The VDR column above describes the fraction of that distribution vector's total app installs that were determined to be malicious. What that means is that wile the percentage of malware distributed via the Play Store is high, the percentage of apps in the Play Store that are malware is low.
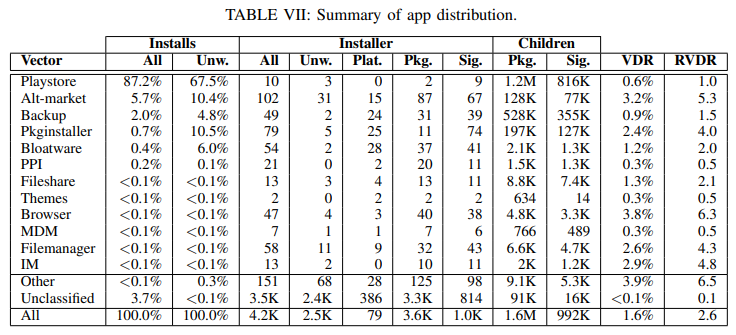
In terms of what the malware actually does, they found that many of the malware examples are designed to show unwanted ads to users, but two significant malware packages included data harvesting apps designed to offload sensitive data to third-party servers. Other packages included tools that could enable an attacker to gain control over the device. In a corporate setting, both of these risks could prove disastrous.
Every mobile threat defense platform Acuity partners with has an answer to this malware issue. In some cases, app data is heuristically inspected against a library of known threats. This catches app IDs that are known malware as well as apps that are using “malware as a service” (yes, that’s really a thing).
Another technique frequently used is to inspect the actual data traffic generated by the apps. In this way an MTD can detect data offloading activities that might be part of a 0-day attack. This method can also block malware that communicates back to malicious servers that have been identified by the MTD platform.
For most of our partners, a combination of techniques is used to ensure that there are a number of processes that can detect malware. Most importantly, when the malware is detected, remediation can be automated to neutralize the thread immediately. Especially for industries constrained by regulatory requirements surrounding the protection of PII, these MTDs can significantly limit liability.
If you’d like to talk about your organization’s approach to mobile security, get in touch with us to set up a quick call. We’re happy to share our experiences and describe some of the solutions available.